FritzBox LAN 2 LAN VPN with pfSense
In this article I described how to set up a FritzBox LAN 2 LAN VPN with StrongSwan. Meanwhile I replaced Ubuntu on the server with pfSense. Of course I have set up my FritzBOX VPN connections again. So here’s a tutorial on how to set up a FritzBox LAN 2 LAN VPN with pfSense.
The prerequisites remain the same in comparison to the StrongSwan instructions:
- Register your FritzBox with a DynDNS service (e.g. https://myfritz.net) and find your FritzBox domain name (e.g. myfb.myfritz.net)
- Find your FritzBox’ private subnet, typically 192.168.178.0/24
- Find (or define) the subnet on the remote site, e.g. 192.168.42.0/24
- Find the hostname of the remote site, e.g. remote.example.com
- Define a secret secret, e.g. S3cret123! (no, please do not use that, that’s my secret secret!)
Configure your FritzBox
Last time I presented a large configuration file that had to be imported into the FritzBox to set up the VPN connection. In the meantime I have found which encryption and hashing algorithms the FritzBox uses by default, so that we can simply use the default settings of the FritzBox and therefore the web interface built into FritzOS 7.x:
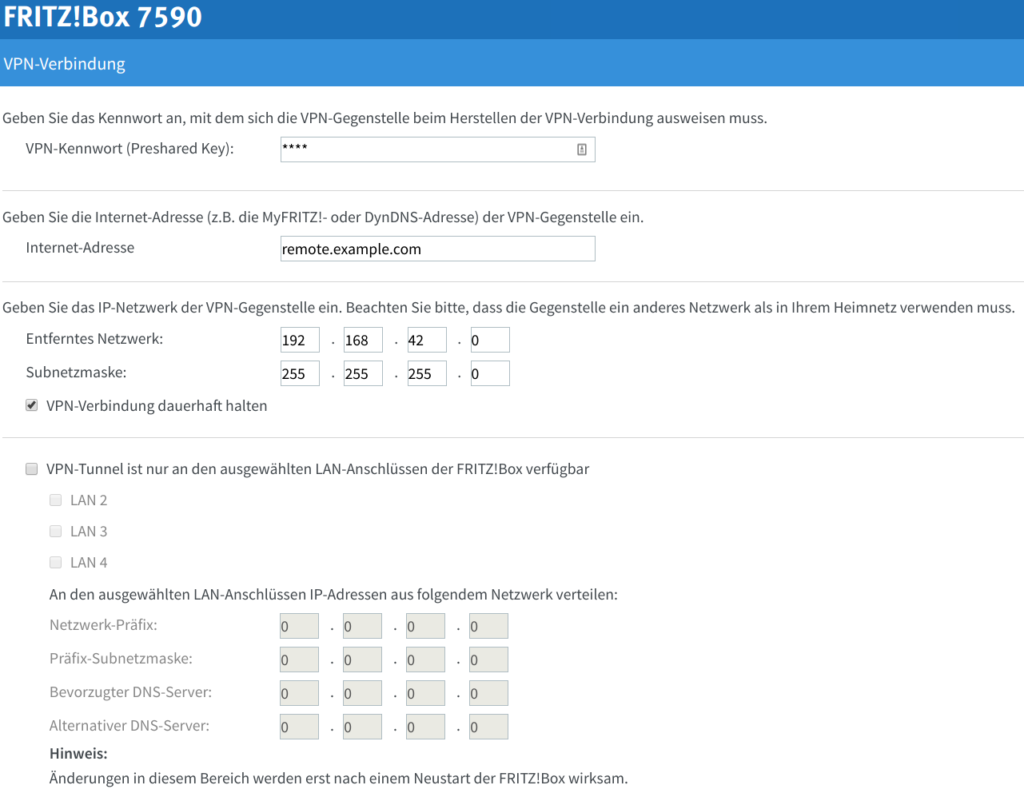
Configure pfSense
The pfSense configuration is similarly simple:
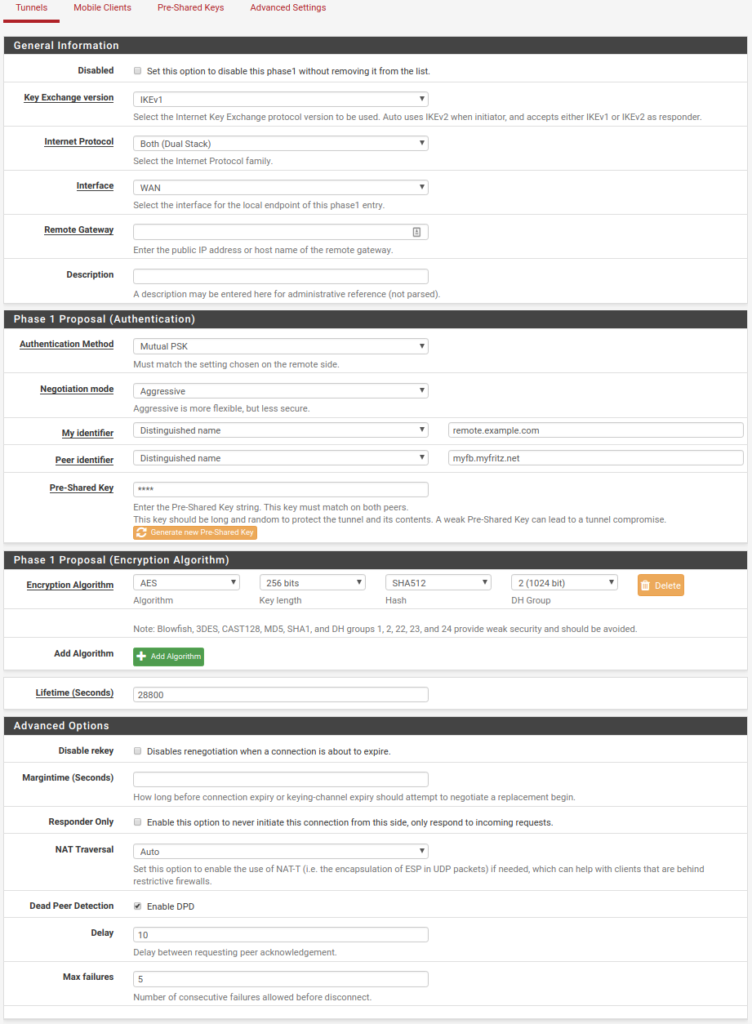
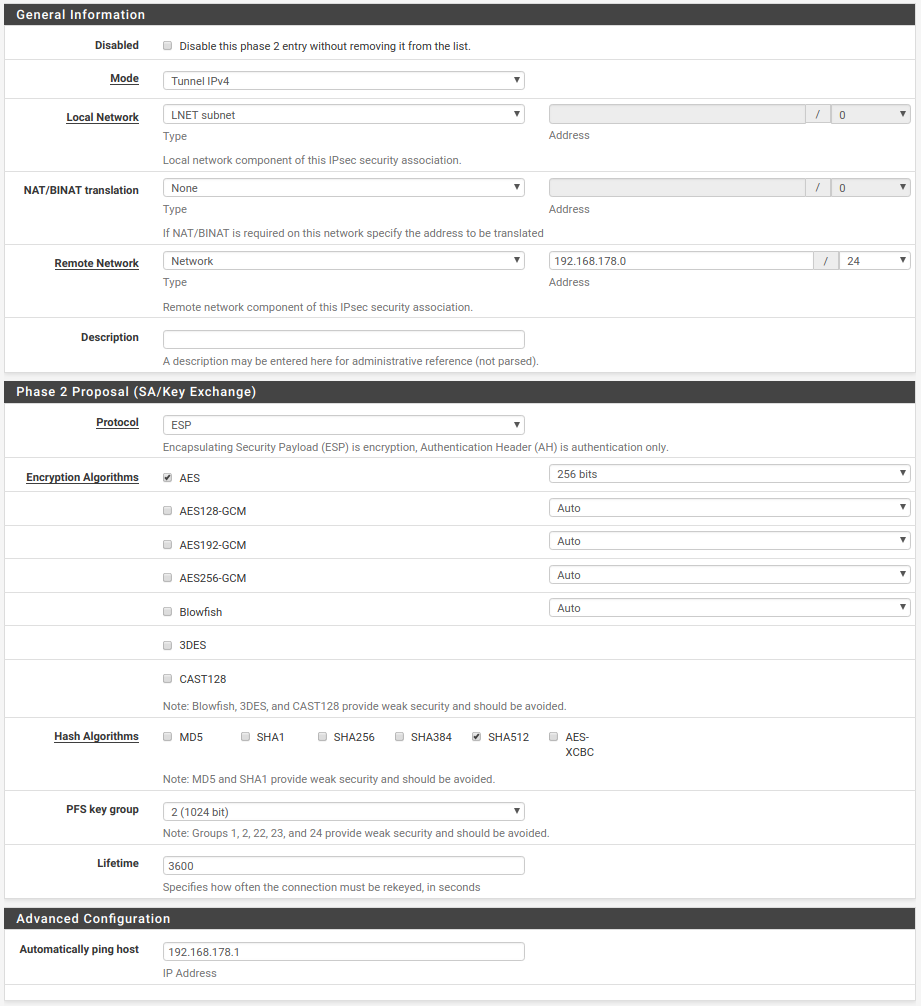
Conclusion
In my opinion, it’s pretty easy to set up a FritzBox LAN 2 LAN VPN with pfSense. The only hard thing is to figure out the preferred encryption and hashing algorithms supported by the FritzBox.
I have this running now with pfSense 2.4.4 with both a FritzBox 7490 and a FritzBox 7590.
An additional note: Sometimes does a Dual Stack connection not seem to be completely stable. In this case it helps to set Internet Protocol to IPv4 in phase 1.

21 COMMENTS
How did you configure FritzBox 7490?
I cannot figure out the basic setup; which Key-ID to use?
Actually, it’s quite easy: pfSense’s “My Identifier”/”Distinguished Name” should be the same (host)name you enter in the FritzBox’ “Internet-Adresse”. It’s basically the hostname of your pfSense gateway. I guess entering an IP address should also be possible, but as far as I know it has to be the same value on both sides, so if you use an IP address for “Internet-Adresse”, you should enter this IP address also as “My Identifier”/”Distinguished Name”.
pfSense’s “Peer Identifier”/”Distinguished Name” has to be the (primary) external hostname of your FritzBox. I’ve only tried it with MyFritz DynDNS service, so the MyFritz name (123randomlettersxyz.myfritz.net) is the right one here. With other DynDNS services try its respective hostname.
Please let me know if you got it working 🙂
…did not manage to get it working. But using OpenVPN Site to site is surprisingly easy and sufficient till wireguard makes it into the bds kernels…
from my fritz!box network a can see lan pc on pfsense but from pfsense i cant see any pc on fritz!box
What do you mean with “see”?
PING, BROWSE etc.
From my Fritz(network) I can connect to servers and computers in pfsense network, but from pfsense network I cant connect to other side(Fritz Network)
Could be a routing issue. Please check your Outbound NAT settings/firewall configuration. Or maybe the target system blocks pings. Please notice: I can’t ping my FritzBox from pfSense, but i can access its webinterface (no idea why).
Hi Matthias!
Is your setup still running? I cannot get the tunnel to establish between my 7590 and the pfSense box….I tried everything you said and 1000 other things. No luck.
Yes, without any problems.
Thanks a lot works well!!!
Hi Matthias,
it works perfectly with modern FritzBoxes running OS 7 e.g. 7.21.
Also it seems to work basically for my older Fritzbox 7390 running on FritzOS 6.86. I had to change both phases to use 3des and SHA-1.
But the connection there seems to be reestablished after e.g. around 200 seconds.
Do you know better parameters? I got it working this far also without a specific config file. Just with the paramters set in the FritzBox standard GUI.
Hi,
sorry, no idea.
Best regards
Matthias
THX work perfeclty
Thanks – perfectly works on first attempt! Saved a lot of time 🙂
Since pfSense 2.5.0, my IPsec link to the Fritz!Box is down. Also with you?
I didn’t try with pfSense 2.5 yet.
Seit dem Update der pfsense auf Version 2.5.0 wird der Tunnel in der pfsense immer als “inactive” angezeigt. Der Tunnel funktioniert aber. Im Status unter IPSEC hat sich die Anzeige auch verändert, die pfsense zeigt dort eine bestehende Verbindung und eine getrennte Verbindung die sich nicht nicht man. verbinden lässt.
Hi. interesting article, but I’m looking how to enable traffic between my home and a lan behind a second VPN, with this scheme:
LAN A IPSec LAN B OpenVPN LAN C
192.168.18.x —- 10.0.7.x —- 192.168.17.x —- 10.0.8.x —- 192.168.10.x
(FritzBox) (pfSense) (pfSense)
Now I’m able to connect from a A to B, from B to A and C, from C to B. But I’d like to enable transparent traffic between LAN A and LAN C. Is this feasible? I’m sure pfSense has no limit on this, but I’ve some doubts for FritzBox.
Theoretically, this shouldn’t be a problem. Guess you need to put the right routes in all the routers, to let the routers know in which direction to forward the traffic if the subnet is not directly known to them. Even in a FritzBox you can add static routes.
P.S. FritzBox is 7490, pfSense is 2.3.5 on LAN B, and 2.4.x on LAN C (both not upgradable).
I guess pfSense device are already configured in the right way. But I can’t figure out how to do this in FritzBox. With FritzBox, until now, I used the config file above (but if the access to LAN C could be archived with web interface, it’s sounds even better).
vpncfg {
connections {
enabled = yes;
conn_type = conntype_lan;
name = “VPN AB Studio”;
always_renew = yes;
reject_not_encrypted = no;
dont_filter_netbios = yes;
localip = 0.0.0.0;
local_virtualip = 0.0.0.0;
remoteip = 192.168.17.1; // IP pfSense su LAN
remote_virtualip = 0.0.0.0;
remotehostname = “pfsenseddns”; // sostituire con DDNS pfSense
localid {
fqdn = “avmddns.myfritz.net”; // sostituire con DDNS FritzBox
}
remoteid {
fqdn = “pfsenseddns”; // sostituire con DDNS pfSense
}
mode = phase1_mode_aggressive;
phase1ss = “dh14/aes/sha”;
keytype = connkeytype_pre_shared;
key = “Pre-Shared Key”; // sostituire con la stessa Pre-Shared Key messa in pfSense (meglio se lunga e con caratteri casuali)
cert_do_server_auth = no;
use_nat_t = yes;
use_xauth = no;
use_cfgmode = no;
phase2localid {
ipnet {
ipaddr = 192.168.18.0; // sostituire con LAN dietro il FritzBox
mask = 255.255.255.0;
}
}
phase2remoteid {
ipnet {
ipaddr = 192.168.17.0; // sostituire con LAN dietro pfSense
mask = 255.255.255.0;
}
}
phase2ss = “esp-all-all/ah-none/comp-all/pfs”;
accesslist = “permit ip any 192.168.17.0 255.255.255.0”; // sostituire con LAN dietro pfSense
}
ike_forward_rules = “udp 0.0.0.0:500 0.0.0.0:500”, “udp 0.0.0.0:4500 0.0.0.0:4500”;
}